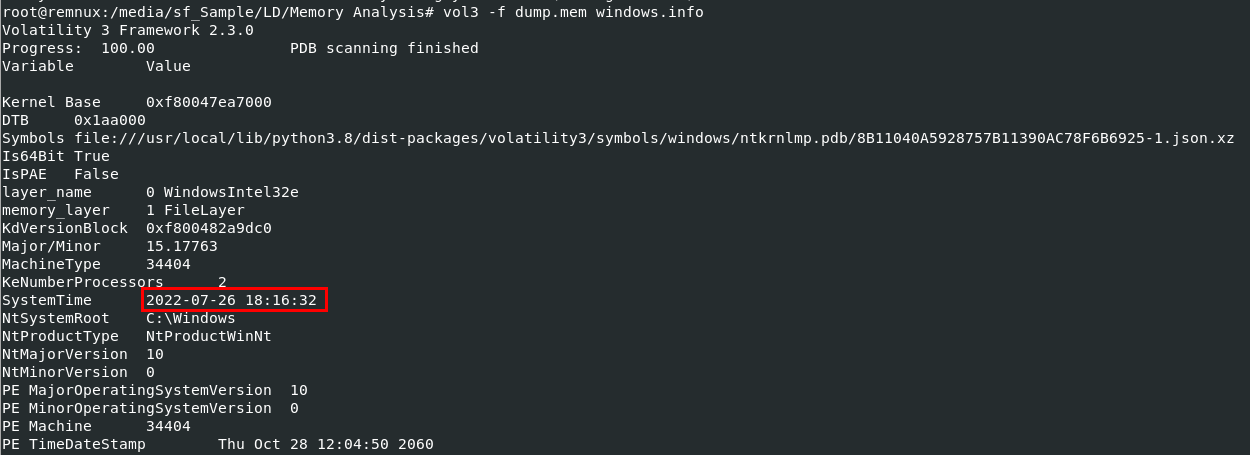
 Volatility 2 didn't work well with this memory image (i tried) so I ended up with
Volatility 2 didn't work well with this memory image (i tried) so I ended up with vol3 -f dump.mem windows.info to get SystemTime Created: 24/05/2024 16:41 Last Updated: 07/06/2024 08:29
A Windows Endpoint was recently compromised. Thanks to our cutting-edge EDR/IDS solution we immediately noticed it. The alert was escalated to Tier 2 (Incident Responders) for further investigation. As our Forensics guy, you were given the memory dump of the compromised host. You should continue to investigate.
~~File link:~~ ~~Download~~ File location: /root/Desktop/ChallengeFile/MemoryDump.zip File Password: infected
NOTE: You can use the Volatility for analysis.
This challenge prepared by 0xCyberJunkie.sh
What was the date and time when Memory from the compromised endpoint was acquired?
 Volatility 2 didn't work well with this memory image (i tried) so I ended up with
Volatility 2 didn't work well with this memory image (i tried) so I ended up with vol3 -f dump.mem windows.info to get SystemTime
2022-07-26 18:16:32
What was the suspicious process running on the system? (Format : name.extension)
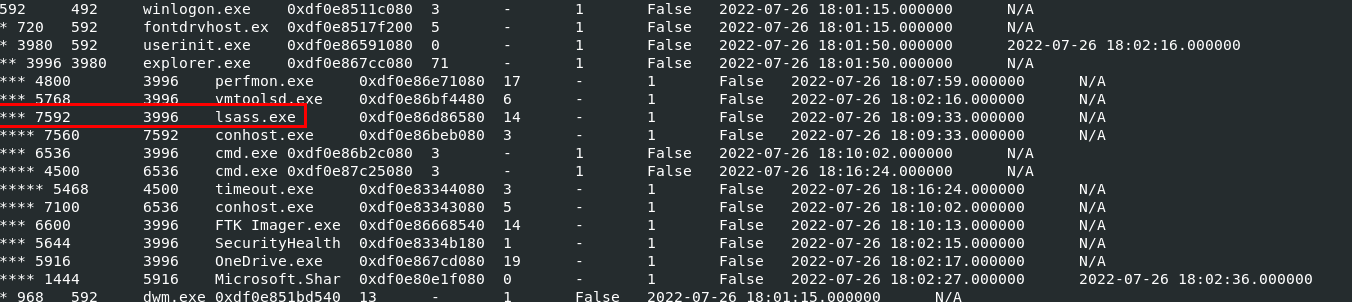 I used
I used vol3 -f dump.mem windows.pstree and this lsass process is suddenly caught my eyes because it couldn't be the chlid process of explorer.exe
lsass.exe
Analyze and find the malicious tool running on the system by the attacker (Format name.extension)
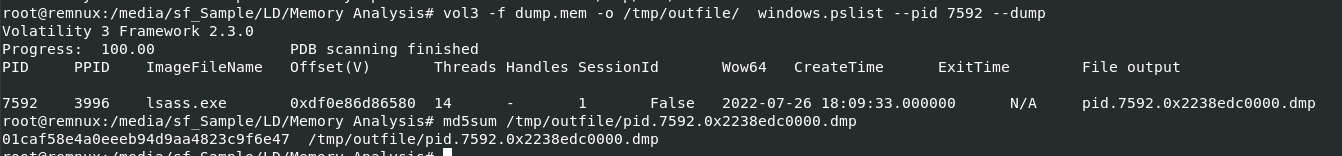 Lets drump it with
Lets drump it with vol3 -f dump.mem -o /tmp/outfile/ windows.pslist --pid 7592 --dump then use md5sum /tmp/outfile/pid.7592.0x2238edc0000.dmp to calculate MD5 so we can use this hash to search on VirusTotal
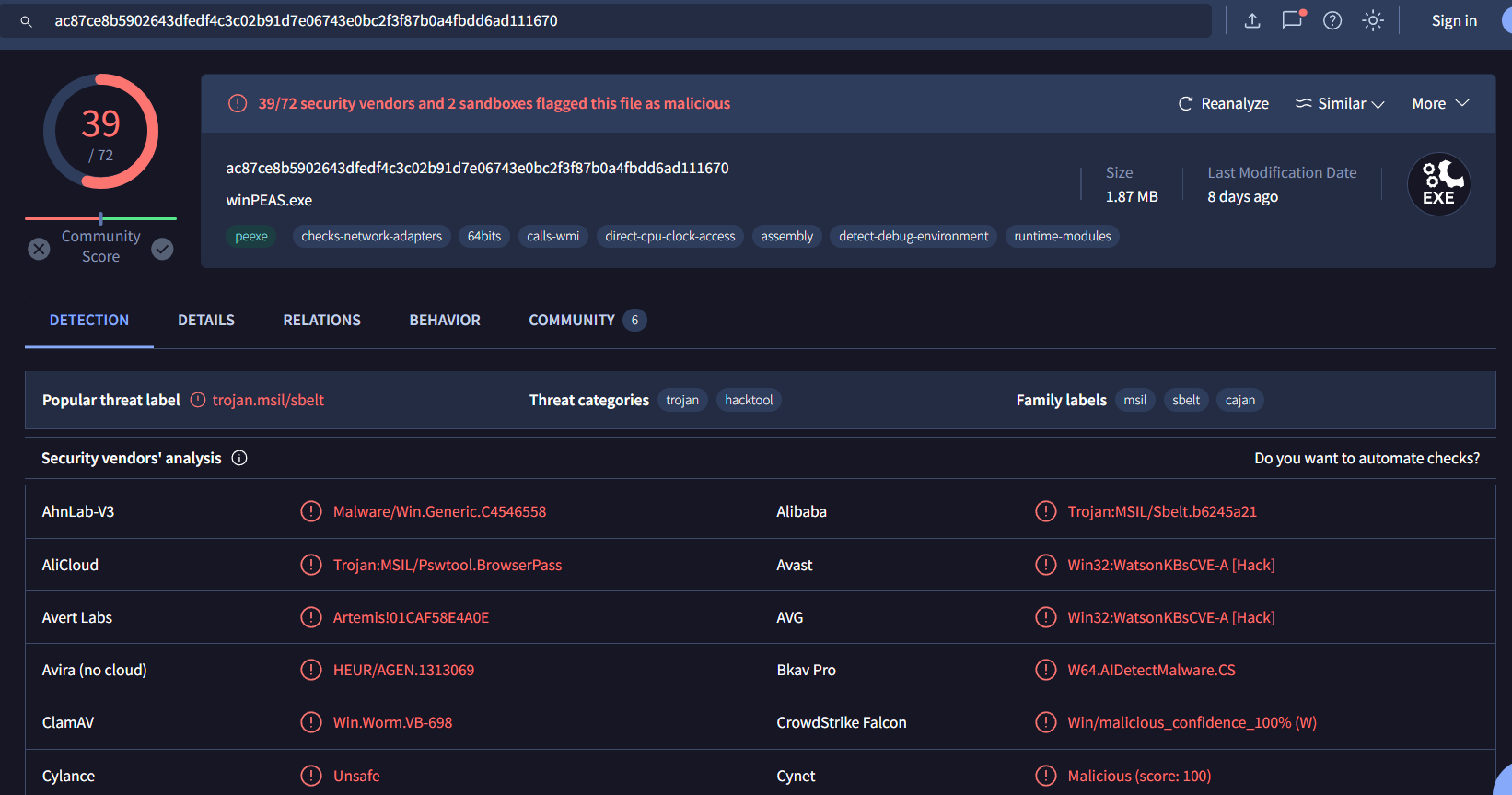 It's winPEAS, so the attacker tried to gain system/admin privilege or enumerate system using this tool
It's winPEAS, so the attacker tried to gain system/admin privilege or enumerate system using this tool
winPEAS.exe
Which User Account was compromised? Format (DomainName/USERNAME)
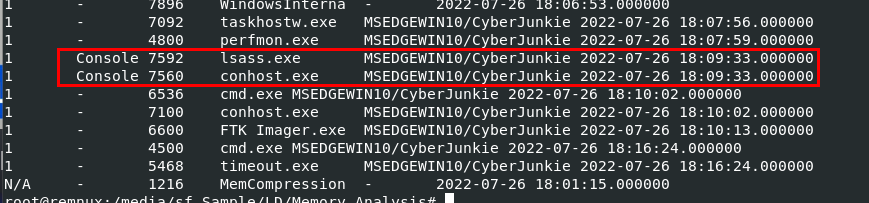 We will use
We will use vol3 -f dump.mem windows.sessions to determine if that suspicious process has a session under any username, which there is
MSEDGEWIN10/CyberJunkie
What is the compromised user password?
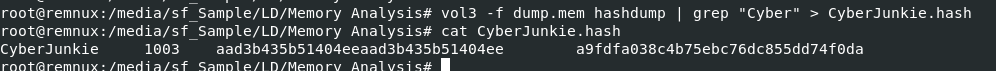 I used hashdump plugin then filter for specific user and pipe it to a file with this
I used hashdump plugin then filter for specific user and pipe it to a file with this vol3 -f dump.mem hashdump | grep "Cyber" > CyberJunkie.hash
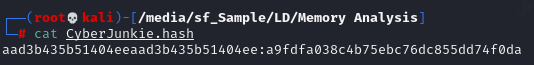 Then I made a little adjustment before using john to crack it
Then I made a little adjustment before using john to crack it
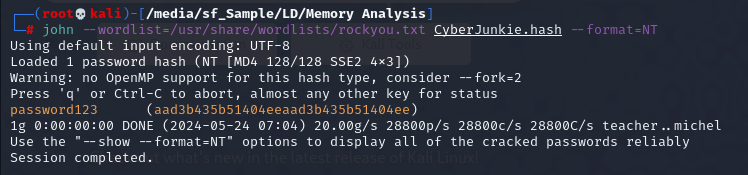 Using
Using john --wordlist=/usr/share/wordlists/rockyou.txt CyberJunkie.hash --format=NT then we have his password
password123